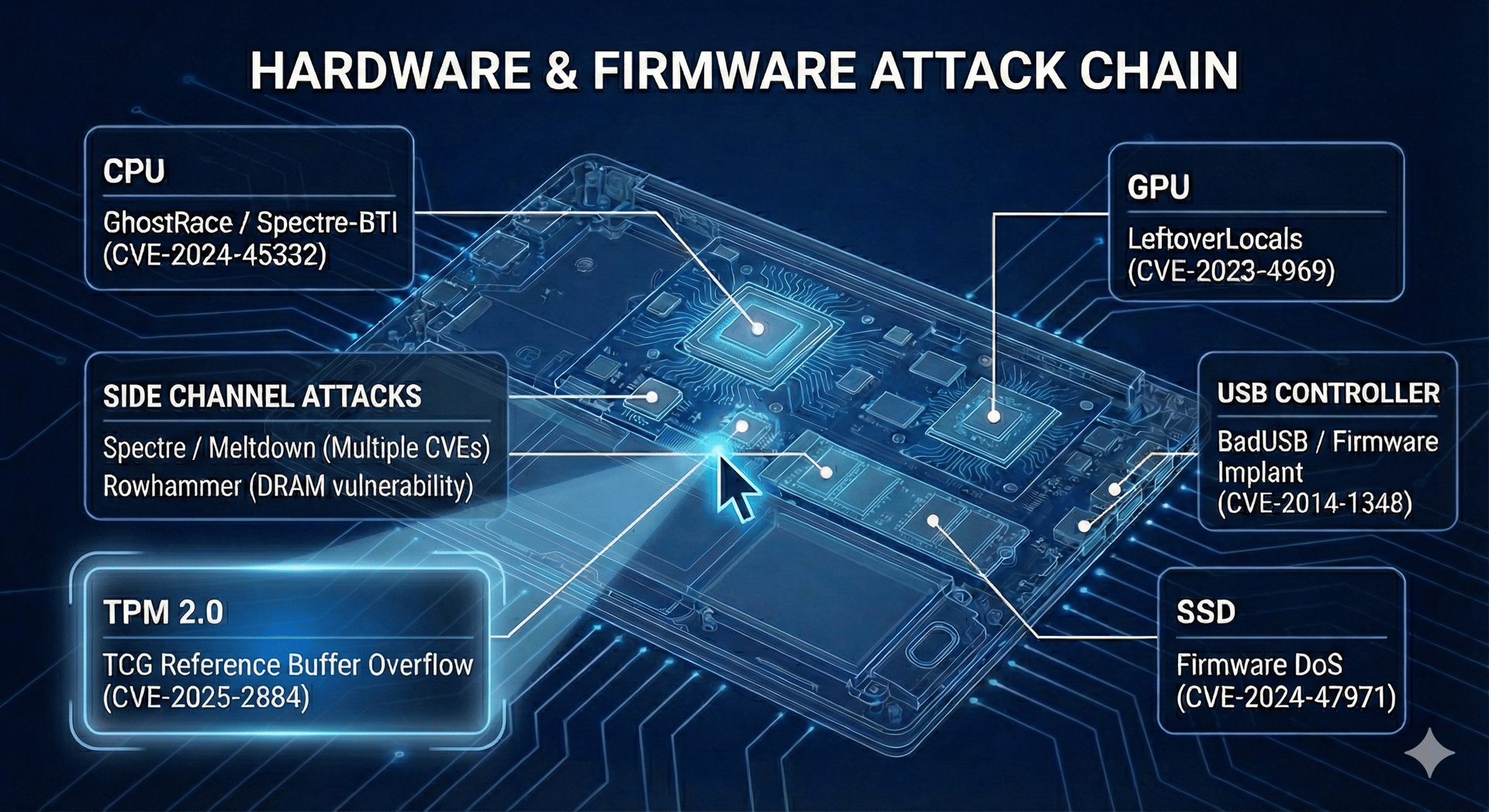
Attack Chain
Dive deep into hardware and firmware vulnerabilities with our interactive attack chain breakdown.

Understanding Hardware Attacks
Attack Chain breaks down complex hardware vulnerabilities into clear, actionable insights for security pros.


A must-have resource for hardware security.
J. Lee
"
Our Services
Dive deep into hardware, firmware, and software vulnerabilities with us.
Firmware Assurance
Firmware Assurance provides deep attestation and visibility to Below-OS measurements.
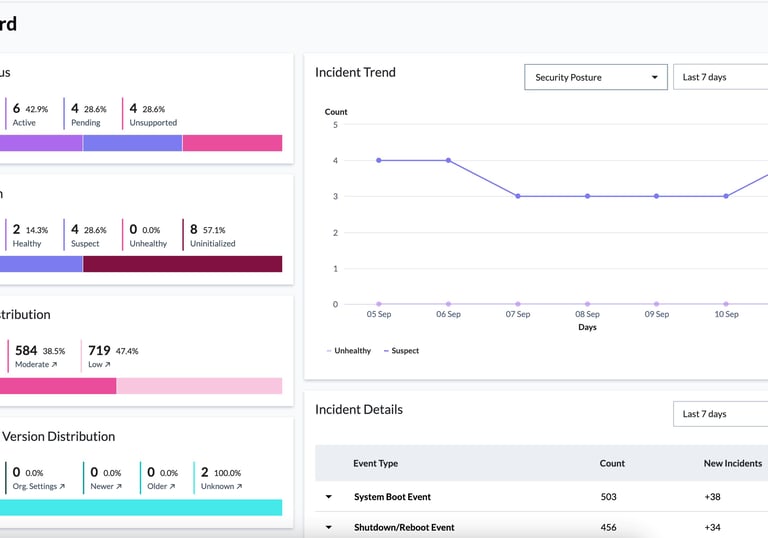
Component Map
Interactive visuals linking laptop and server parts to their specific security risks.
Track vulnerabilities in UEFI, microcode, and embedded controllers in real time.
CVE Tracker



